This blog post covers my experience at DEF CON 33's Quantum Village, focusing on the quantum key distribution (QKD) data interception challenge and solution.
DEF CON 33 - Quantum Village - The Shapiro Incident

DEF CON 33 - Quantum Village - The Entropy Heist
This blog post covers my experience at DEF CON 33's Quantum Village, focusing on the post-quantum cryptography ML-DSA-65 "The Entropy Heist" challenge and solution.
Building My Own Cryptographic Badge Add-on - NSEC 2024
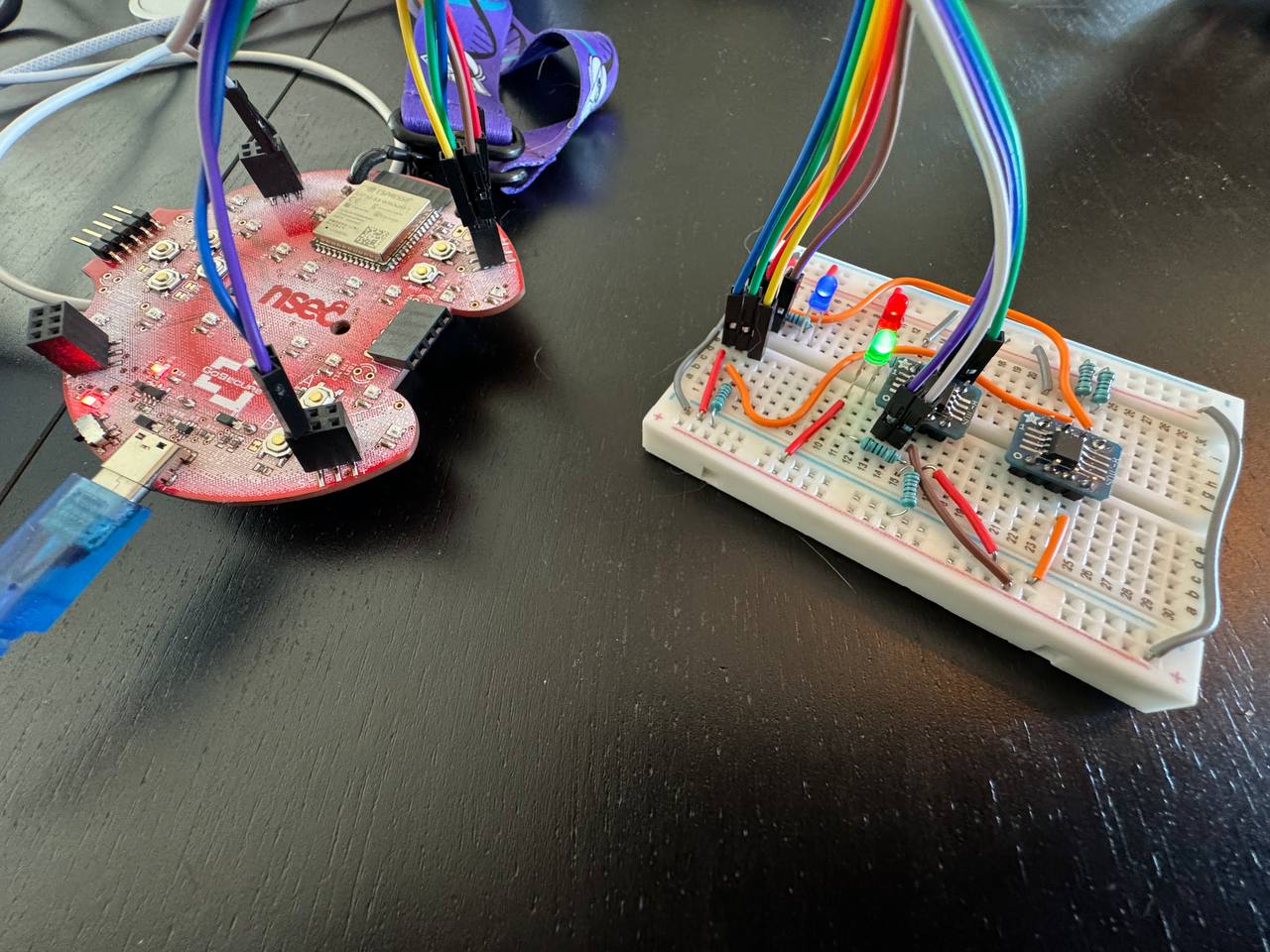
This blog post goes through the custom build of the NSEC 2024 badge Phospholipid addon. As part of the CTF, for successfully dumping the addon's flash, a set of raw components was provided to build our own version. This will cover the journey to get the cryptographic coprocessor working with the original NSEC badge.
NSEC 2024 - Badge Addon - Phospholipid
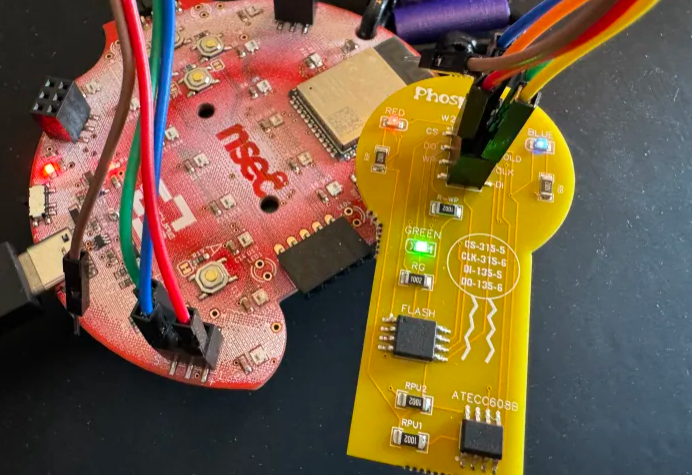
This blog post provides a detailed walkthrough of the NSEC 2024 hardware badge addon (Phospholipid) track, diving into the intricacies of the W25Q64JV chip and memory protection, and working with the ATECC608B cryptographic chip to solve a Elliptic Curve Diffie-Hellman (ECDH) challenge.
Building a Production-Grade Minecraft Cloud Infrastructure

Journey of building a production-grade Minecraft server in the cloud, including management, monitoring, and observability - all for free!
Post-Quantum Cryptography - Practical Kyber Experimentation
Continuing down the rabbit hole of PQC investigating the Kyber implementation more directly, then using experimental branches of common tooling to explore practical implementation of post-quantum cryptography.
