Introduction

Over the last couple years I’ve started dabbling in locksport. Learning the basics of how a lock works has shown interesting parallels to the cybersecurity world. From identifying weaknesses in the locking mechanism, how people abuse these weaknesses to bypass security, security mechanisms added in to address these weaknesses, and ultimately the continuous loop of cat and mouse; of offensive and defensive security escalations.
Participants at Northsec 2022 CTF this year we were presented with an interesting safe cracking challenge. Talking with the organizers after the CTF they mentioned that this was originally planned as part of the physical track of the CTF, however due to circumstances had to adjust the offering to a digital variant. While I was a bit dejected this wouldn’t be a hands-on challenge, since I had separately already started looking into practice safes to start playing with, this was a great opportunity to start learning the theory and understand how to approach this physically in the future.
Challenge Description
MikhailVolkov:
I saw my office painting slightly crooked than usual. Since my safe is behind the painting, it immediately raised my suspicion.
I found thisstrange piece of paperon my safe containing highly sensitive documents.
I am not going to open my safe with you guys close by.
Since you claim to be good at security, validate for me if someone had an access to my safe.
Note: flag is in FLAG-\d{2}-\d{2}-\d{2} format
The challenge starts out with a missive - the Ouyaya company member believes someone could have broken into their safe and accessed sensitive documents. There was some cryptic letter left on top the safe and they provided us a copy of it. Let’s start this challenge off and take a look at the mysterious note.
Before going into the challenge I had not looked worked with safe cracking. Someone with that background should be able to immediately identify what this means, however I had to start at the basics and start looking online with “where do I start?!”.
Safe Cracking Theory
I quickly found a video playlist that really helped clarify not only what to look for, but even went into the underlying theory, explaining how safes work mechanically, where the weaknesses are introduced, and ultimately how to extract the right numbers from an analysis.
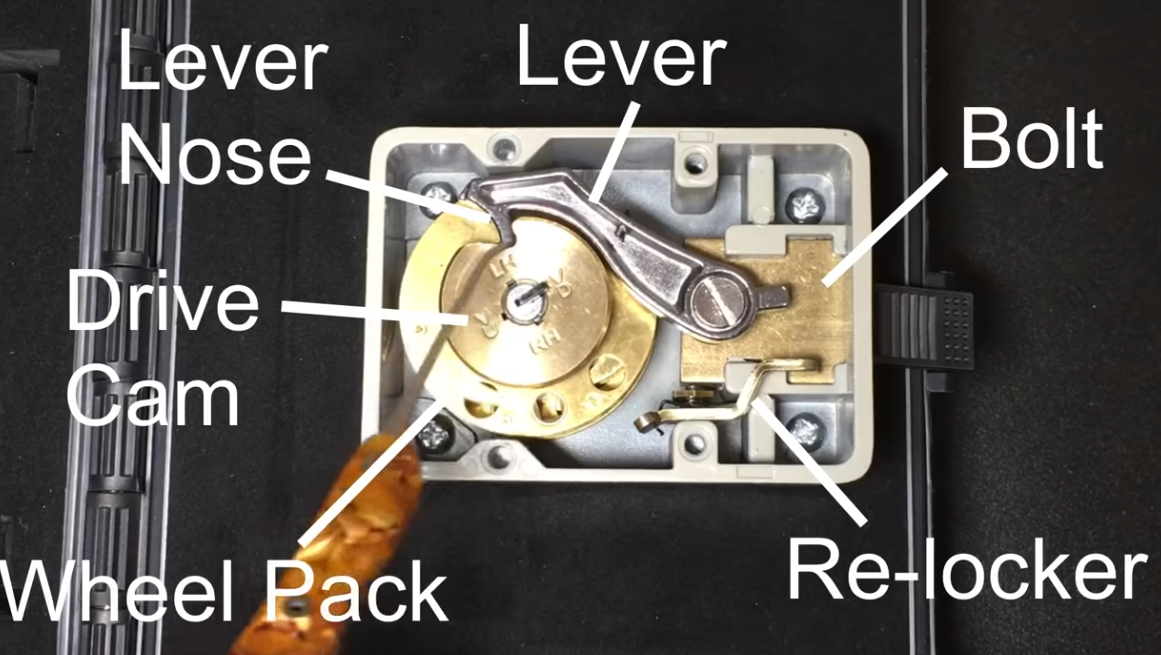
In addition to the series above there was a video review of a Sparrow Challenge vault that provided a good view at the internals of how a safe works.
With a little bit more digging, I read through the the Sparrow Manual on learning how to crack their practice vault. This page specifically jumped out at me for a few reasons.
It really seems like the provided file are the notes some master safe cracker left behind. We see the 0-100 starting index, the contact points, and the wheel numbers at the top. Looks to me like a lot of the hard work has been done for us already and we just need to understand and interpret the data left behind.
Mapping Data
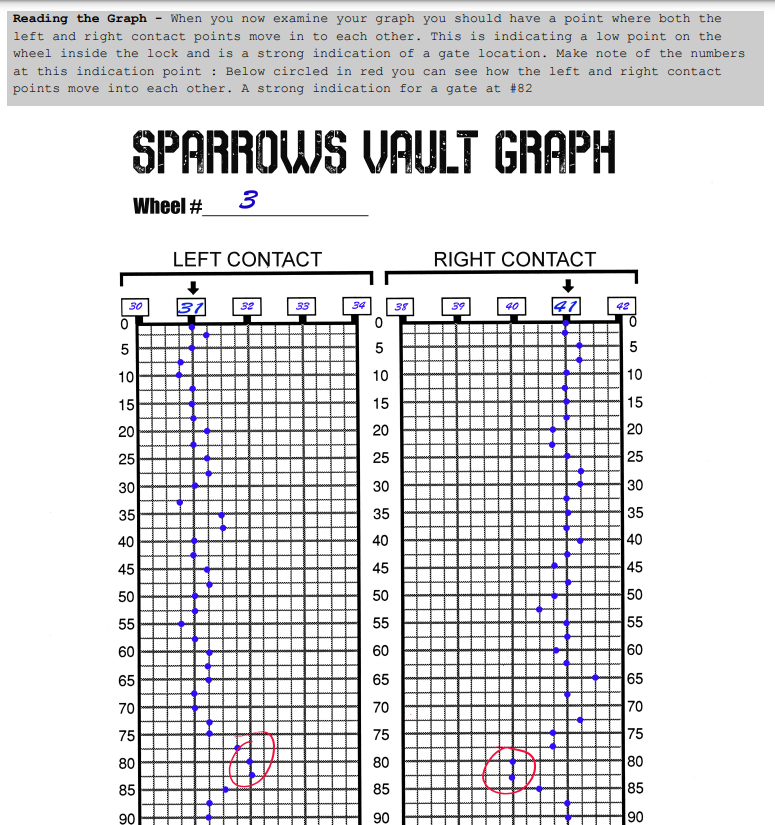
Similar to how we would approach a real safe to crack let’s start with wheel number three. We can interpret the columns as the left and right contact points being mapped. To bring it into a similar format to what we viewed in the videos I graphed it out in excel.
Great, that looks pretty solid. The next step is to try and see where the contact points have a convergence from the basis, towards each other. There is one specific point where that seems more clear than anywhere else.
Based off of this since the contact point is 42.5 I believe the third wheel’s number is either 42 or 43. In reality we could be more granular on the safe itself and go by individual numbers instead of by 2.5, however we have to work with the data provided, so let’s hope it ends up being one of the two.
Victory
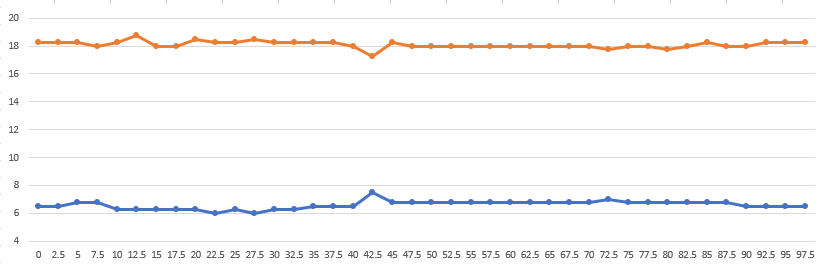
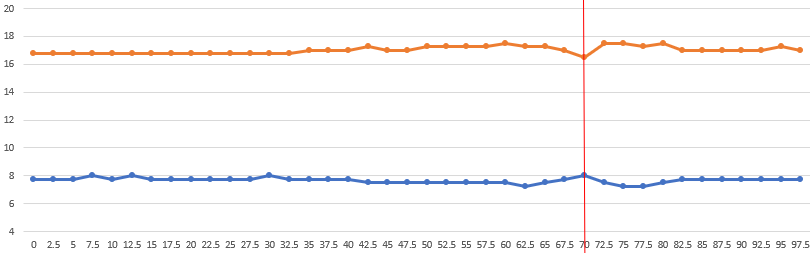
If we continue the approach for the second wheel, we graph out the data and check for the convergence.
Excellent, so the second wheel should be 70.
For the first wheel, we weren’t given any contact point data. We just see an x in the first four columns. If you think about it this makes sense, as we have the first two numbers, this should in theory be a matter of finding the final numbers by process of elimination. With that assumption - our first wheel should somewhere between 8, 9, 10.
We don’t have an exact number based of this, but the permutations we need to try are reduced to a handful!
Side Note on Headache
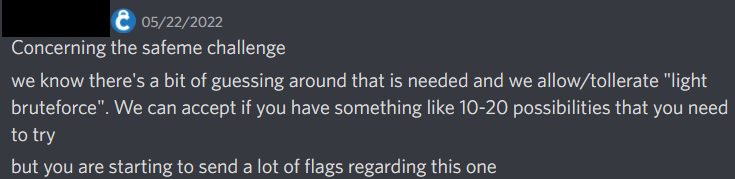
In reality, I didn’t get the numbers 42.5 and 70 initially. The reason? I had forgotten to change the axis label from index to value. So while I had the same graphs, and the same correct “convergence”, I was trying to use 18 and 29 instead…
I was certain I had the right numbers, and while trying the various permutations I decidedly tripped one of the monitors on the NSEC admin team. Thankfully they were understanding and since it wasn’t an automated bruteforcing left me off with a nice “hey, stop it”.
Submission
After way too much time, I had an “aha” moment and realized what I had done wrong with the index vs. value blunder while graphing. With that corrected, and the right numbers gathered I was at:
- Wheel 3 -
[42,43] - Wheel 2 -
70 - Wheel 1 -
[8,9,10]
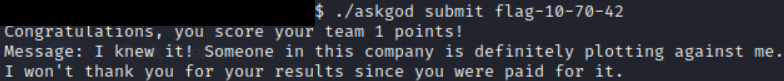
With a smaller number of permutations I hoped not to invoke the wrath of the NSEC admins and tried them out. Thankfully within a few different tries I was rewarded!
Summary
Considering learning Safe Cracking was something on my “to do” list, I was pleasantly surprised to see this challenge during the NSEC CTF. This offered me a good opportunity to learn the basics, understand how it works, and if nothing else has reinvigorated my interest. Looking closer at the Sparrow practice vault I would say it is quite probable that it will end up in my arsenal in the near future. This would help reinforce what I learned during the CTF, and move it from the theoretical to the practical on how to recognize the contact points.
As always, I am thankful to the NSEC team for not only the event, and quality of challenges offered - that alone is a massive testament to the effort the team put into preparing and running the event, but I am also thankful for their understanding and willingness to reach out to clarify my “bruteforcing” attempts with the incorrect number. Where I initially felt defeated as I was certain it was the right number, I was able to continue, realize the mistake, and correct it successfully. Thank you (and again, sorry!) for making that a possibility.
Thanks folks, until next time!